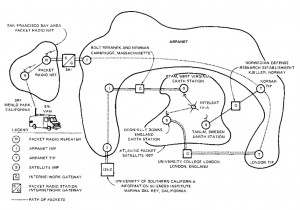
On October 27, 1980, the ARPANET — the Internet’s earliest incarnation — had its first epic fail. I’m not talking about your garden-variety system glitch: I’m talking about a spectacular, network-wide outage. The entire network was offline for hours.
Today it’s hard to even comprehend the idea of the entire Internet crashing (and when I try, it makes me feel slightly nauseated). But we face other kinds of online disasters, and when they happen, we need our own strategies for rebooting.
In social media, the disasters people talk about most are fundamentally crises of public relations. These fall into two types: crises that originate in social media, and crises that originate offline. In the era of Twitter, YouTube and Facebook, both types of crisis require a rapid, social media response.
Looking at the most recent social media crises is one way to think about the kinds of challenges for which you need to prepare. But social media has a way of ensuring that each crisis is different from the last, so if you’re prepared to handle a YouTube meltdown, you’ll probably get served with a FourSquare nightmare.
That’s why it pays to look for principles of online crisis management that will be relevant in the long run. And by examining the 1980 ARPANET crash, we can do just that: identify the questions the ARPANET team might have asked 31 years ago, and which your team could answer today.
- In conventional histories, it’s a well-worn trope to talk about how the Internet was designed to withstand nuclear attack; how its entire design was based on ensuring that even if one part of the network went down, the others would survive. From this flow all sorts of near-religious beliefs about the Internet’s propensity for authentic, peer-to-peer communications and its resistance to central authority. But the ARPANET crash points us to a moment in living memory when the Internet was far from unstoppable. What beliefs about the Internet is your social media strategy based on? How do you know whether those beliefs are well-founded?
- It’s striking that 31 years after the ARPANET crash, Google Scholar doesn’t contain a single in-depth academic study focusing specifically on this historic crash (perhaps because by the time journal articles became digital, it had ceased to be a technically relevant case). I obviously can’t speak to the technical interest that the crash might or might not hold for today’s computer scientists, security experts and network administrators, but it’s hard to believe that this incident doesn’t hold social or historical significance. Even if the only thing we can learn from the 1980 crash is the thinking process that led early network administrators to overlook this potential vulnerability, it would seem well worthwhile to examine the social, organizational and cognitive context in which the ARPANET was able to fail. What crucial online mistakes have you left un- or underexamined, and what could you learn from them?
- Today, the crash of your individual computer (typically on the 11th page of a 12-page, unsaved document) falls somewhere between annoyance and bummer on the scale of human misery. The short-term crash of your company’s site or internal server usually falls somewhere between inconvenience and embarrassment. The crash or overload of a significant portion of the global internets is somewhere between distracting and worrying (depending on what it portends for network security). But the prospect of a global, system-wide network crash is only at one extreme or the other: laughable (because what could possibly crash the whole Internet?) or heart-stopping (because imagine what could possibly crash the whole Internet). What scope of failure can you tolerate in your social media presence? What level of misery would a failure induce?
- A 1981 analysis of the crash noted that the problem might have been prevented, but a prevention system would have required lots of processing power and memory and “[s]ince CPU cycles and memory are both potentially scarce resources, this did not seem to us to be a cost-effective way to deal with problems that arise, say, once per year.†This feels like an amusing explanation today, when processing power and memory are dirt cheap.  What a great reminder that every crisis prevention or problem-solving strategy is based on a set of resource constraints and assumptions. But our strategies often fail to evolve as quickly as the underlying assumptions may change. If you have a strategy for preventing or managing potential online problems — for example, handling critical tweets — what assumptions does your strategy rest on? And how often do you stop to assess whether those assumptions still hold — and if not, to update your strategy?
- When the network went down, administrators realized they had a system-wide problem when they got phone calls from ARPANET sites all over the country. In the absence of the network itself, phone was the alternative channel of first resort, and in 1980, the network was small enough that phone-based communication was a viable option for getting an overall picture of the network. In today’s you may have to cope with losing access to key tools for your online response. What is your alternative channel of first resort? How would you communicate during a social media crisis if you couldn’t use social media tools to help?
- An error in a single bit brought the ARPANET to a halt. Call this the Death Star principle: if you focus only on preparing for the big problems, a tiny X-wing fighter can sneak in and blow up your entire space station. What tiny problems could occur for your social media activities? Which tiny problems could potentially blow up your whole strategy?
If you can answer these questions, you’ll have established the basic principles for your social media crisis management strategy. What questions would you add to the list?